We have all seen the news, there is a war on, one that does not leave thousands of bodies in graves but still destroys lives. This was is bloodless, but still makes the news on a weekly basis. The targets are global, every county, every person and every business. No one is safe, as the attackers can strike from across the globe in the middle of the night. This is the Information War.
We have seen companies like Sony struck down, expensive firewalls broken through like iron gates from the castles of old. Many of these security breaches have made the news in the last year, including Home Depot, Target, and even the US Department of Defense… all have lost battles in this war.
As a result, new tools are being invented that strengthen defenses from the inside. The Solaris operating system is one of these tools, a powerful defense against attacks from all vectors. Several technologies are built into the heart of the operating system, fused into the DNA of the Operating Systems;
- Built in compliance, a tool that reports on the Operating System’s security against best practices
- Immutable Zones, allowing read only Virtual machines, freezing the Operating Systems and hardware configuration from changes
- And audit Service, that sends an audit log to a secure Audit Vault where logs can securely stored and analyzed
-
A minimal installation mode, resulting in a strong lean Operating System
-
Time-based and location-based access control to PAM services, allowing access only from certain locations and during specific time windows.
-
An integrated firewall, protecting each OS independently as needed
-
File integrity verification, verifying that file integrity is maintained for each and every file on the server.
-
Package verification , protecting packages from being changed before they are installed
-
And more
Combine these features, and your servers are safer than ever, helping to repel both internal and external attackers. But the first rule of security, is never stop. New vectors and new vulnerabilities are being discovered or created daily. Any solid security policy must continue to analyze and adapt.
This first entry in this series will focus on the compliance tool, which gathers information about a server and reports against the server’s configuration against best practices.
Solaris 11.2 shipped with a new command compliance, that lets you run system assessments against compliance benchmarks, and then generate reports reports from those. While it currently works against a single host, you can use Metric Extension in Enterprise Manager to consolidate the reports, more on that later. Oracle is also working on an enhancement that will allow for multiserver reporting.
By default two compliance benchmarks are shipped, once the standard Solaris baseline, and a second more strict policy that conforms to the PCI DSS v 2.0 standard, primarily used by companies that process credit card data. You can check what benchmarks are installed by using the compliance command;
root@solaris:/# compliance list -bv
pci-dss
Payment Card Industry Data Security Standard
solaris
Oracle Solaris Security Policy
root@solaris:/#
This example will focus on the Solaris Policy, but for additional security; you can either use the pci-dss policy or create your own policy.
With the baseline analysis, seven core areas are checked;

Using the compliance tool, we can run reports, and then assessment that produce an html or XCCDF (Extensible Configuration Checklist Description Format) report. These can then be looked at, or imported into a database for further analysis.
To run the standard report, we simple use the command “compliance assess” which will run an assessment against the default solaris benchmark. We can also specify a different benchmark, using the –p option. In the following example, we will run against the solaris benchmark.
root@solaris:/# compliance assess -b solaris
Assessment will be named 'solaris.Baseline.2015-01-12,18:46'
Package integrity is verified
Test_1.1
fail
The OS version is current
Test_1.2
pass
Package signature checking is globally activated
Test_1.3
pass
All local filesystems are ZFS
Test_2.1
pass
Find and list .forward files
Test_2.4
pass
Find and list .netrc files
Test_2.5
pass
Find and list .rhosts files
Test_2.7
pass
Service svc:/system/coreadm is enabled
Test_3.1
pass
Service svc:/system/cron is enabled
Test_3.2
pass
Service svc:/system/cryptosvc is enabled
Test_3.3
pass
Service svc:/system/dbus is enabled
Test_3.4
pass
Service svc:/system/hal is enabled
Test_3.5
pass
Service svc:/system/identity:domain is enabled
Test_3.6
pass
Service svc:/system/intrd is enabled
Test_3.7
pass
Service svc:/system/keymap is enabled
Test_3.8
pass
Service svc:/system/picl is enabled
Test_3.9
pass
Service svc:/system/scheduler is enabled
Test_3.10
pass
Service svc:/system/system-log is enabled
Test_3.11
pass
Service svc:/system/utmp is enabled
Test_3.12
pass
Service svc:/system/zones is enabled
Test_3.13
pass
Service svc:/system/zones-install is enabled
Test_3.14
pass
Service svc:/network/rpc/bind is enabled
Test_3.15
pass
Service svc:/system/name-service/switch is enabled
Test_3.16
pass
Service svc:/system/name-service/cache is enabled
Test_3.17
pass
Service svc:/network/nfs/status is disabled or not installed
Test_3.18
pass
Service svc:/network/nfs/nlockmgr is disabled or not installed
Test_3.19
pass
Service svc:/network/nfs/client is disabled or not installed
Test_3.20
pass
Service svc:/network/nfs/server is disabled or not installed
Test_3.21
pass
Service svc:/network/nfs/fedfs-client is disabled or not installed
Test_3.22
fail
Service svc:/network/nfs/rquota is disabled or not installed
Test_3.23
pass
Service svc:/network/nfs/cbd is disabled or not installed
Test_3.24
pass
Service svc:/network/nfs/mapid is disabled or not installed
Test_3.25
fail
Service svc:/network/smb/client is disabled or not installed
Test_3.26
pass
Check ftp is disabled, or not installed
Test_3.27
pass
Service svc:/network/ssh is enabled
Test_3.28
pass
Service svc:/network/smtp:sendmail is enabled
Test_3.29
fail
Service svc:/network/sendmail-client is enabled
Test_3.30
pass
Service svc:/network/inetd is enabled
Test_3.31
pass
Service svc:/system/filesystem/autofs is enabled
Test_3.32
pass
Service svc:/system/power management is enabled
Test_3.34
pass
Service svc:/network/dns/multicast is disabled or not installed
Test_3.35
pass
Service svc:/network/dhcp-server is disabled or not installed
Test_3.36
pass
Service svc:/network/rarp is disabled or not installed
Test_3.38
pass
Service svc:/network/slp is disabled or not installed
Test_3.39
pass
Service svc:/network/security/kadmin is disabled or not installed
Test_3.40
pass
Service svc:/network/security/krb5_prop is disabled or not installed
Test_3.41
pass
Service svc:/network/security/krb5kdc is disabled or not installed
Test_3.42
pass
Service svc:/application/management/net-snmp is disabled or not installed
Test_3.43
pass
Service svc:/application/cups/in-lpd is disabled or not installed
Test_3.44
pass
Service svc:/application/stosreg is enabled
Test_3.45
pass
Service svc:/system/ocm is enabled
Test_3.46
pass
Service svc:/network/finger is disabled or not installed
Test_3.47
pass
Service svc:/network/login:rlogin is disabled or not installed
Test_3.48
pass
Service svc:/network/login:klogin is disabled or not installed
Test_3.49
pass
Service svc:/network/login:eklogin is disabled or not installed
Test_3.50
pass
Service svc:/network/shell:default is disabled or not installed
Test_3.51
pass
Service svc:/network/shell:kshell is disabled or not installed
Test_3.52
pass
Service svc:/network/telnet is disabled or not installed
Test_3.53
pass
Service svc:/network/uucp is disabled or not installed
Test_3.54
pass
Service svc:/network/chargen:stream is disabled or not installed
Test_3.55
pass
Service svc:/network/chargen:dgram is disabled or not installed
Test_3.56
pass
Service svc:/network/daytime:stream is disabled or not installed
Test_3.57
pass
Service svc:/network/daytime:dgram is disabled or not installed
Test_3.58
pass
Service svc:/network/discard:stream is disabled or not installed
Test_3.59
pass
Service svc:/network/discard:dgram is disabled or not installed
Test_3.60
pass
Service svc:/network/echo:stream is disabled or not installed
Test_3.61
pass
Service svc:/network/echo:dgram is disabled or not installed
Test_3.62
pass
Service svc:/network/time:stream is disabled or not installed
Test_3.63
pass
Service svc:/network/time:dgram is disabled or not installed
Test_3.64
pass
Service svc:/network/comsat is disabled or not installed
Test_3.65
pass
Service svc:/network/rexec is disabled or not installed
Test_3.66
pass
Service svc:/network/talk is disabled or not installed
Test_3.67
pass
Service svc:/network/stdiscover is disabled or not installed
Test_3.68
pass
Service svc:/network/stlisten is disabled or not installed
Test_3.69
pass
Service svc:/network/rpc/gss is enabled if and only if Kerberos is configured
Test_3.70.2
fail
Service svc:/network/rpc/rstat is disabled or not installed
Test_3.74
pass
Service svc:/network/rpc/rusers is disabled or not installed
Test_3.75
pass
Service svc:/network/rpc/meta is disabled or not installed
Test_3.76
pass
Service svc:/network/rpc/metamed is disabled or not installed
Test_3.77
pass
Service svc:/network/rpc/metamh is disabled or not installed
Test_3.78
pass
Service svc:/network/rpc/rex is disabled or not installed
Test_3.79
pass
Service svc:/network/rpc/spray is disabled or not installed
Test_3.80
pass
Service svc:/network/rpc/wall is disabled or not installed
Test_3.81
pass
Service svc:/system/avahi-bridge-dsd is disabled or not installed
Test_3.82
pass
Service cde-ttdbserver is enabled, or not installed
Test_3.83
pass
Service svc:/application/graphical-login/gdm is enabled or not installed
Test_3.84
pass
Service cde-calendar-manager is enabled, or not installed
Test_3.85
pass
Service svc:/application/x11/xfs is disabled or not installed
Test_3.86
pass
Service xvnc-inetd is enabled, or not installed
Test_3.87
pass
The GNOME desktop has suitable screensaver settings
Test_3.88
pass
The NIS client service is disabled or not installed
Test_3.89
pass
The NIS server service is disabled or not installed
Test_3.90
pass
The r-protocols services are disabled in PAM
Test_3.91
fail
Service svc:/network/http:apache22 is disabled or not installed
Test_3.92
pass
Service svc:/network/rpc/keyserv is disabled or not installed
Test_3.93
pass
ssh(1) is the only service binding a listener to non-loopback addresses
Test_3.95
pass
ssh(1) requires passwords
Test_3.96
pass
rhost-based authentication in ssh(1) is disabled
Test_3.97
pass
root login by using ssh(1) is disabled
Test_3.98
pass
Service svc:/network/smtp:sendmail only listens on loopback
Test_3.99
pass
The umask(1) for SMF services is 022
Test_3.100
pass
Directed broadcasts are not forwarded
Test_4.1
pass
Responses to ICMP netmask requests are disabled
Test_4.2
pass
Responses to ICMP broadcast timestamp requests are disabled
Test_4.3
pass
Responses to ICMP timestamp requests are disabled
Test_4.4
pass
Source-routed packets are not forwarded
Test_4.5
pass
TCP reverse source routing is disabled
Test_4.6
pass
The maximum number of half-open TCP connections is set to the default
Test_4.7
pass
The maximum number of waiting TCP connections is set to the default
Test_4.8
pass
Responses to echo requests on multicast addresses are disabled
Test_4.9
fail
Strong TCP packet sequence numbering
Test_4.13.2
pass
DICTIONBDIR is set to /var/passwd
Test_5.1
pass
Passwords are hashed with the SHA-256 algorithm
Test_5.2
pass
Passwords allow repeat characters
Test_5.4
pass
Passwords require at least two alphabetic characters
Test_5.5
pass
Passwords require at least three characters difference from the previous password
Test_5.6.3
pass
Passwords do not impose restrictions involving lowercase characters
Test_5.8
pass
Passwords require a minimum of one non-alphabetic character
Test_5.9
pass
Passwords do not impose restrictions involving special characters
Test_5.10
pass
NAMECHECK for passwords is set to YES
Test_5.14
pass
Passwords require at least six characters
Test_5.15.6
pass
Passwords allow whitespace
Test_5.16
pass
root is a role
Test_5.17
pass
Role details are unchanged
Test_5.18
pass
Logins require passwords
Test_5.19
pass
shadow(4) password fields are not empty
Test_5.20
pass
Local users are assigned home directories
Test_5.21
pass
root is the only user with UID=0
Test_5.22
pass
All groups specified in /etc/passwd are defined in /etc/group
Test_5.23
pass
Home directories for all users exist
Test_5.24
fail
Reserved system accounts remain unused
Test_5.25
pass
Find and list duplicate GIDs
Test_5.27
fail
Find and list duplicate group names
Test_5.28
pass
Find and list duplicate UIDs
Test_5.29
pass
Find and list duplicate usernames
Test_5.30
pass
Default system accounts are locked
Test_5.31
pass
The default user UMASK is 022
Test_6.1
pass
root access is console-only
Test_6.2
pass
DISABLETIME is set for logins
Test_6.3
pass
SLEEPTIME following an invalid login attempt is set to 4
Test_6.4
pass
Name services are set to all local (files) only
Test_6.5
fail
Address Space Layout Randomization (ASLR) is enabled
Test_6.6
pass
Check all default audit properties
Test_7.1
Pass
Once the assessment is run, we need to generate a report. By default the report will be in html format, but the output can go to log or zccdf formats.
root@solaris:/# compliance report
/var/share/compliance/assessments/solaris.Baseline.2015-01-12,18:46/report.html
The report will give you the details of when it was run, the target host and what benchmark was used;
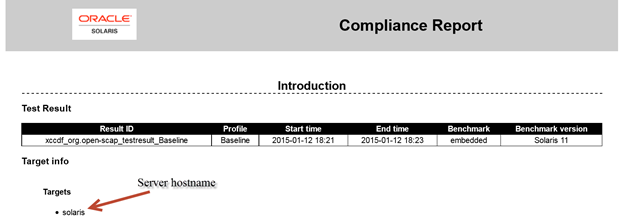
You also get a general score, in this case we were 89.53% compliant

You then get the details summary, listing every test with a pass/fail
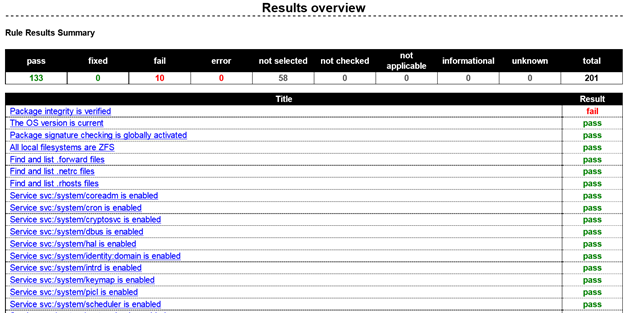
One great feature, is on a fail item, you will often see what command needs to be run to fix the issue.
On this example, we failed the SNMP check;

You can click on the test to see the details; and in this example a simple command the will resolve the issue.
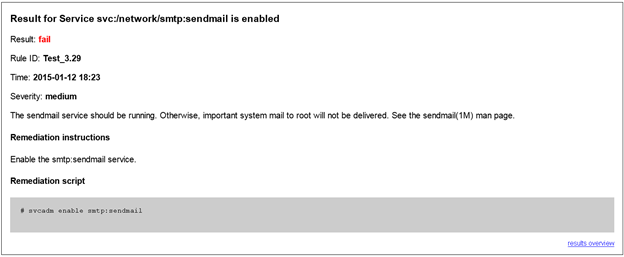
Hopefully you will find this an easy tool to use to improve the configuration security of the operating system. Look for the next entry in this series that covers Immutable Zones.
Pingback: Solaris 11.4, a secure OS for your cloud - Tales from the Datacenter